Configuring OAuth using GlobalConfig
EnRoute Technical Reference
EnRoute can be configured to authenticate requests using OAuth.
Here is a GlobalConfig to configure Google Authentication
Creating Client to configure OAuth in Google API Console
Using Google as an identity provider, needs creating an OAuth Client. Create the OAuth Client using the credentials
Create credentials of type OAuth Client Id
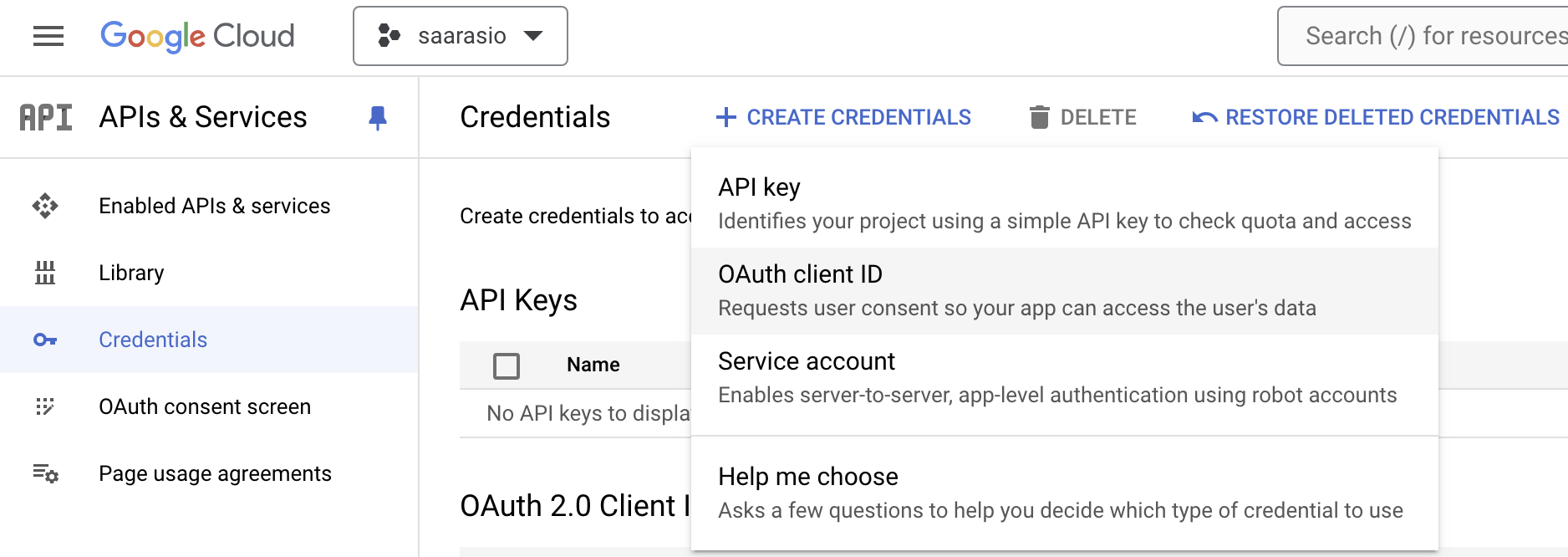
The application type should be web-application
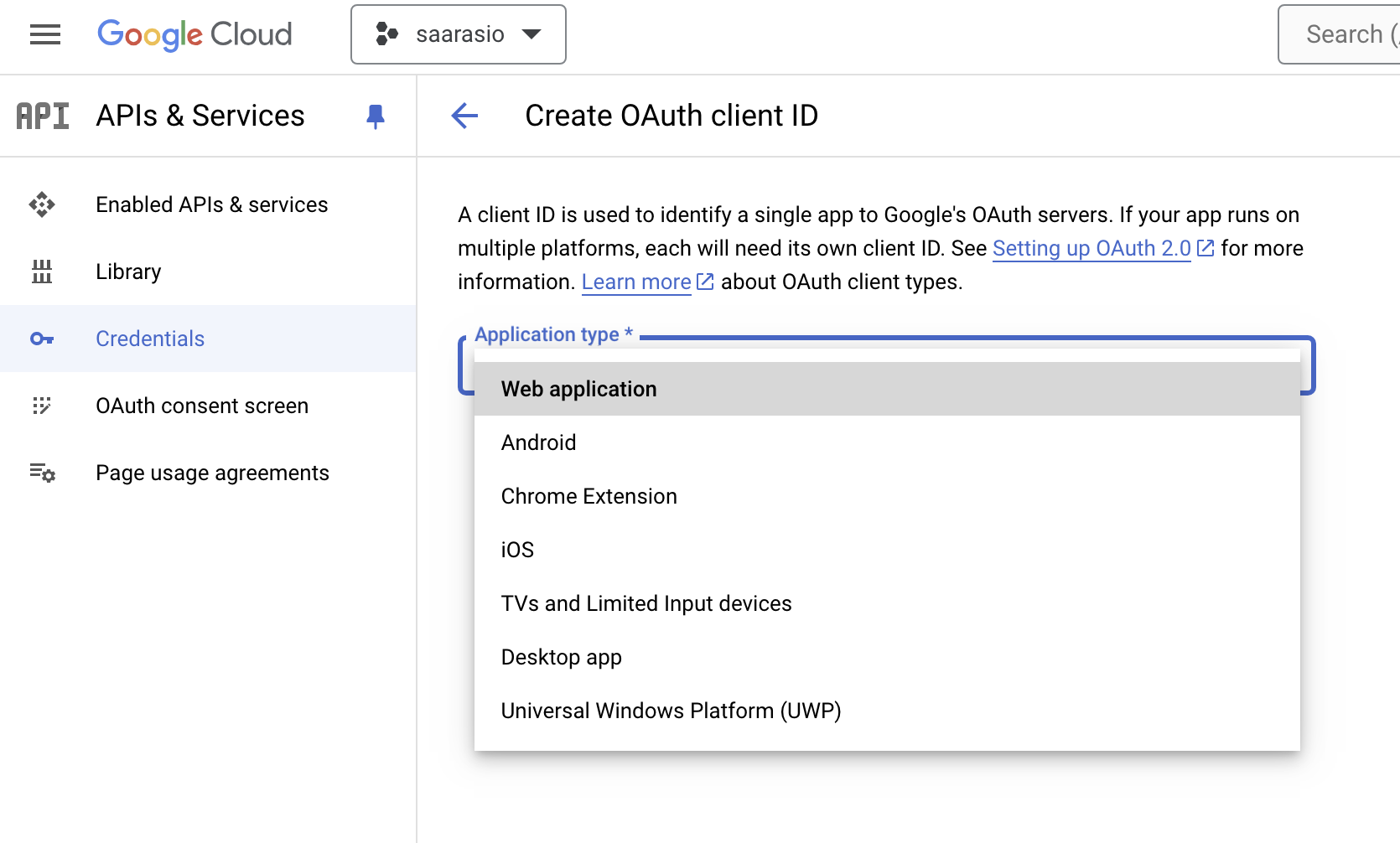
Provide a name and authorized urls. The authorized urls is the domain name of your url and the path on which the application can be accessed
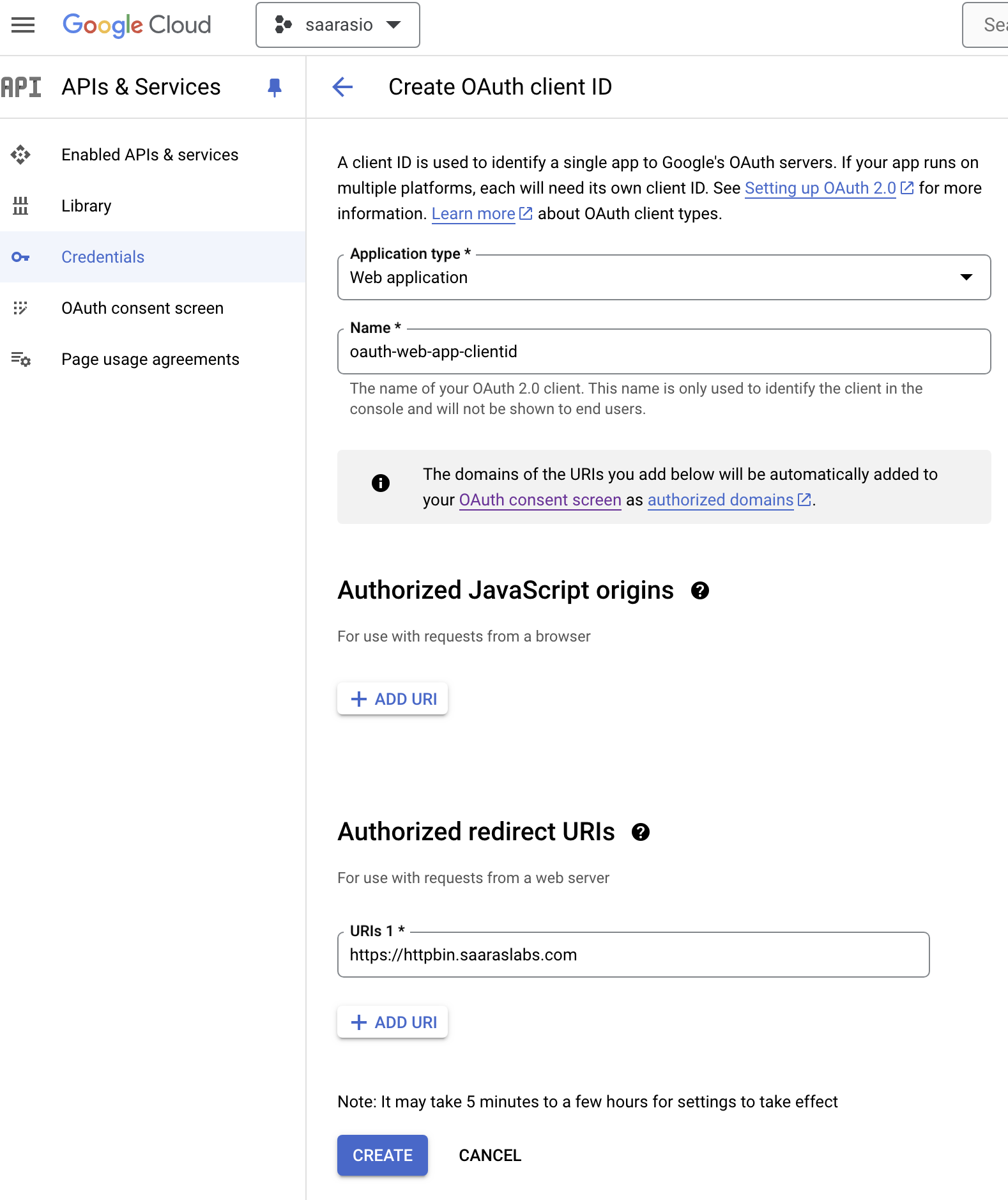
Once the application is created, note the client ID and Client secret. This will be used to configure EnRoute
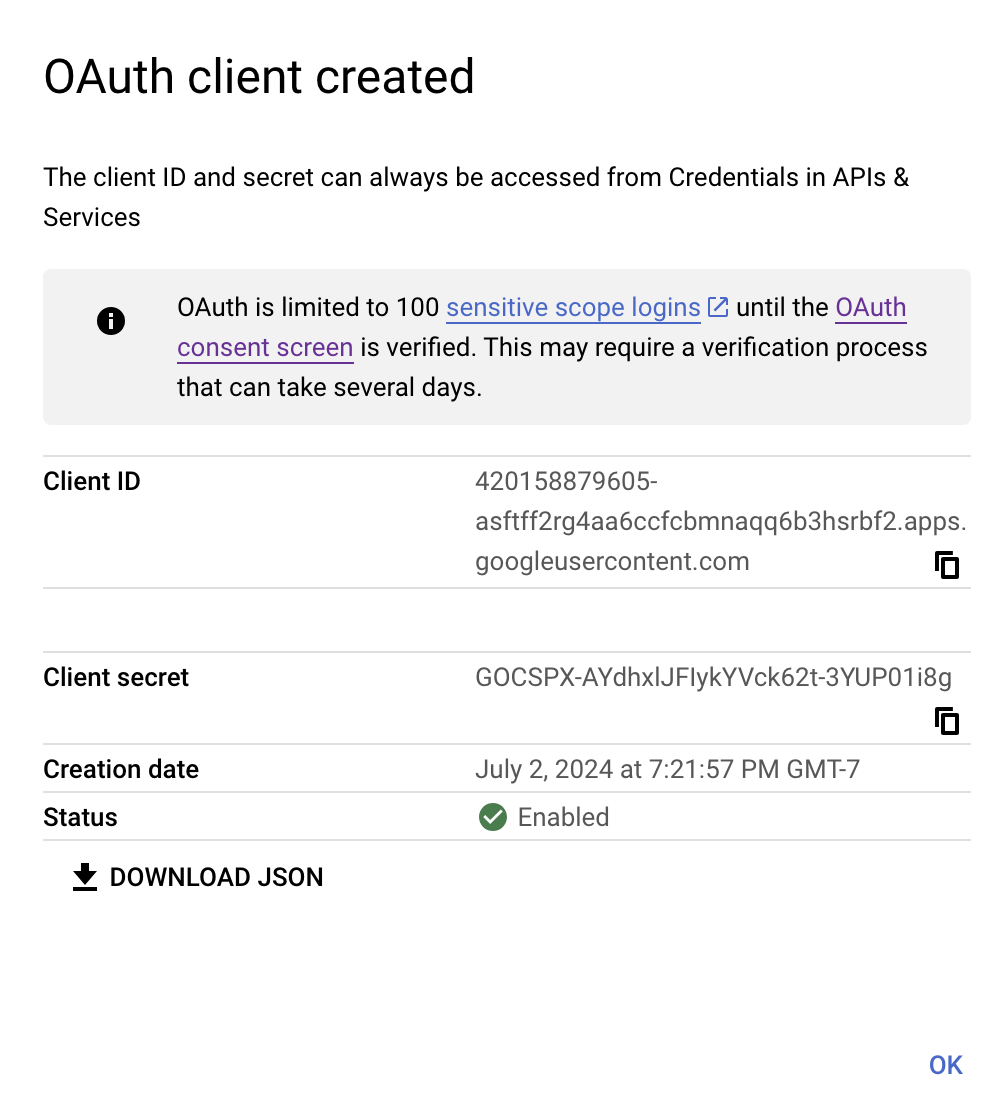
Fetch the OIDC Wellknown config
curl -s https://accounts.google.com/.well-known/openid-configuration
The output of above command is -
{
"issuer": "https://accounts.google.com",
"authorization_endpoint": "https://accounts.google.com/o/oauth2/v2/auth",
"device_authorization_endpoint": "https://oauth2.googleapis.com/device/code",
"token_endpoint": "https://oauth2.googleapis.com/token",
"userinfo_endpoint": "https://openidconnect.googleapis.com/v1/userinfo",
"revocation_endpoint": "https://oauth2.googleapis.com/revoke",
"jwks_uri": "https://www.googleapis.com/oauth2/v3/certs",
"response_types_supported": [
"code",
"token",
"id_token",
"code token",
"code id_token",
"token id_token",
"code token id_token",
"none"
],
"subject_types_supported": [
"public"
],
"id_token_signing_alg_values_supported": [
"RS256"
],
"scopes_supported": [
"openid",
"email",
"profile"
],
"token_endpoint_auth_methods_supported": [
"client_secret_post",
"client_secret_basic"
],
"claims_supported": [
"aud",
"email",
"email_verified",
"exp",
"family_name",
"given_name",
"iat",
"iss",
"name",
"picture",
"sub"
],
"code_challenge_methods_supported": [
"plain",
"S256"
],
"grant_types_supported": [
"authorization_code",
"refresh_token",
"urn:ietf:params:oauth:grant-type:device_code",
"urn:ietf:params:oauth:grant-type:jwt-bearer"
]
}
Note the different endpoints in the above configuration that we’ll be using
Secrets to support OAuth
In this step, we create the Client Secret and HMAC Secret
The Client Secret is the one we received when we created the OAuth Client in the earlier step
kubectl create secret generic clientsecret2 --from-literal=clientsecret=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
The HMAC secret is the one used to create cookies from access token
HMACSECRET=`head -c 32 /dev/urandom`
kubectl create secret generic hmacsecret --from-literal=hmacsecret=$HMACSECRET
ExternalService to connect to Google Authentication Serivce
kind: Service
apiVersion: v1
metadata:
name: google-oauth2
namespace: default
spec:
type: ExternalName
externalName: oauth2.googleapis.com
ports:
- port: 443
protocol: TCP
targetPort: 443
GlobalConfig for OAuth with Google
We now create the GlobalConfig to configure authentication using the client, secret and externalservice created in the step above
apiVersion: enroute.saaras.io/v1
kind: GlobalConfig
metadata:
name: enroute-globalconfig-oauth
namespace: default
spec:
config: |
{
"openid_connect" : {
"provider": {
"authorization_endpoint" : "https://accounts.google.com/o/oauth2/v2/auth",
"token_endpoint" : "https://oauth2.googleapis.com/token"
},
"client_id": "420158879605-7ej53bmc605kssgjucq1jjsrb9irg0bf.apps.googleusercontent.com",
"client_secret" : "clientsecret",
"hmac_secret" : "hmacsecret",
"client_secret_namespace" : "default",
"hmac_secret_namespace" : "default",
"scopes" : ["email"],
"redirect_url" : "%REQ(x-forwarded-proto)%://%REQ(:authority)%/oauth2/callback",
"redirect_path_matcher" : "/oauth2/callback",
"default_signout_path" : "/signout"
},
"external_oauth_service" : {
"name" : "google-oauth2",
"namespace" : "default",
"port" : 443,
"protocol" : "tls"
}
}
name: enroute-globalconfig-oauth
type: globalconfig_oauth
When a GatewayHost is configured for the domain, all the requests will undergo OAuth authentication
apiVersion: enroute.saaras.io/v1
kind: GatewayHost
metadata:
labels:
app: httpbin
name: httpbin-9000-gatewayhost-httpbin-host
namespace: httpbin
spec:
routes:
- conditions:
- prefix: /
services:
- name: httpbin
port: 9000
virtualhost:
fqdn: 'httpbin.saaraslabs.com'
tls:
secretName: saaraslabs