Validate JWT Tokens
EnRoute Technical Reference
JWT Plugin
The Enroute JWT filter/plugin can be used to verify JWT tokens in a request. The plugin is a global plugin and is attached to a service. When attached to a service, specific routes can be protected.
The JWT Plugin talks to an external JWKS provider to fetch the keys used for signing the JWT. The external JWKS provider can be an internal service or an external JWKS provider (eg: Okta, Ping Identity, Auth0 etc.)
The plugin performs JWT validation on a Bearer token present in the HTTP header. If the Bearer token JWT doesn’t validate, an error response with a is returned. Signing keys are loaded from a JWK Set that is loaded over HTTPs.
JWT System Diagram

- User makes a request [1]
- Enroute fetches keys from external JWKs provider (if not cached) [2,3]
- Enroute validates the JWT token using these keys
- If JWT is valid, request is passed to the backend service [4], else 401 Unauthorized is returned
JWT Filter Configuration
JWT filter configuration needs the following config
- An external JWKs provider
- configured as a Service for Kubernetes Gateway
apiVersion: v1
kind: Service
metadata:
name: externalauth
namespace: httpbin
spec:
type: ExternalName
externalName: saaras.auth0.com
ports:
- port: 443
name: https
---
- JWT Filter config
| Field | Description |
|---|---|
| name | Name of Service that provides JWKS. |
| jwks_uri | URI Location of keys |
| audience | Audience for this API |
| issuer | Issuer for this API |
| route | A list of route (match conditions) for which JWT validation is enabled |
| jwt_service_name | Name of the service/upstream configured in previous step to reach jwks uri |
| jwt_service_port | Port on which this service can be reached |
| jwt_forward_header_name | Header in which JWT is forwarded to protected service. Leave empty to disable forwarding of JWT |
| route | Specifies matching prefix and route for which JWT is verified |
apiVersion: enroute.saaras.io/v1
kind: HttpFilter
metadata:
labels:
app: httpbin-app
name: httpbin-80-jwtfilter
namespace: httpbin
spec:
enrouteConfigScope: ["enroute1"]
httpFilterConfig:
config: |
{
"name" : "auth0",
"jwks_uri" : "https://saaras.auth0.com/.well-known/jwks.json",
"audience" : "api-identifier",
"issuer" : "https://saaras.auth0.com/",
"route" : [{"prefix" : "/"}],
"jwt_service_name" : "externalauth",
"jwt_service_port" : 443,
"jwt_forward_header_name" : "x-jwt-token"
}
name: httpbin-80-jwtfilter
services:
name: externalauth
port: 443
protocol: tls
type: http_filter_jwt
JWKS Provider Auth0
This section describes how Enroute can be configured to use Auth0 as JWKS provider
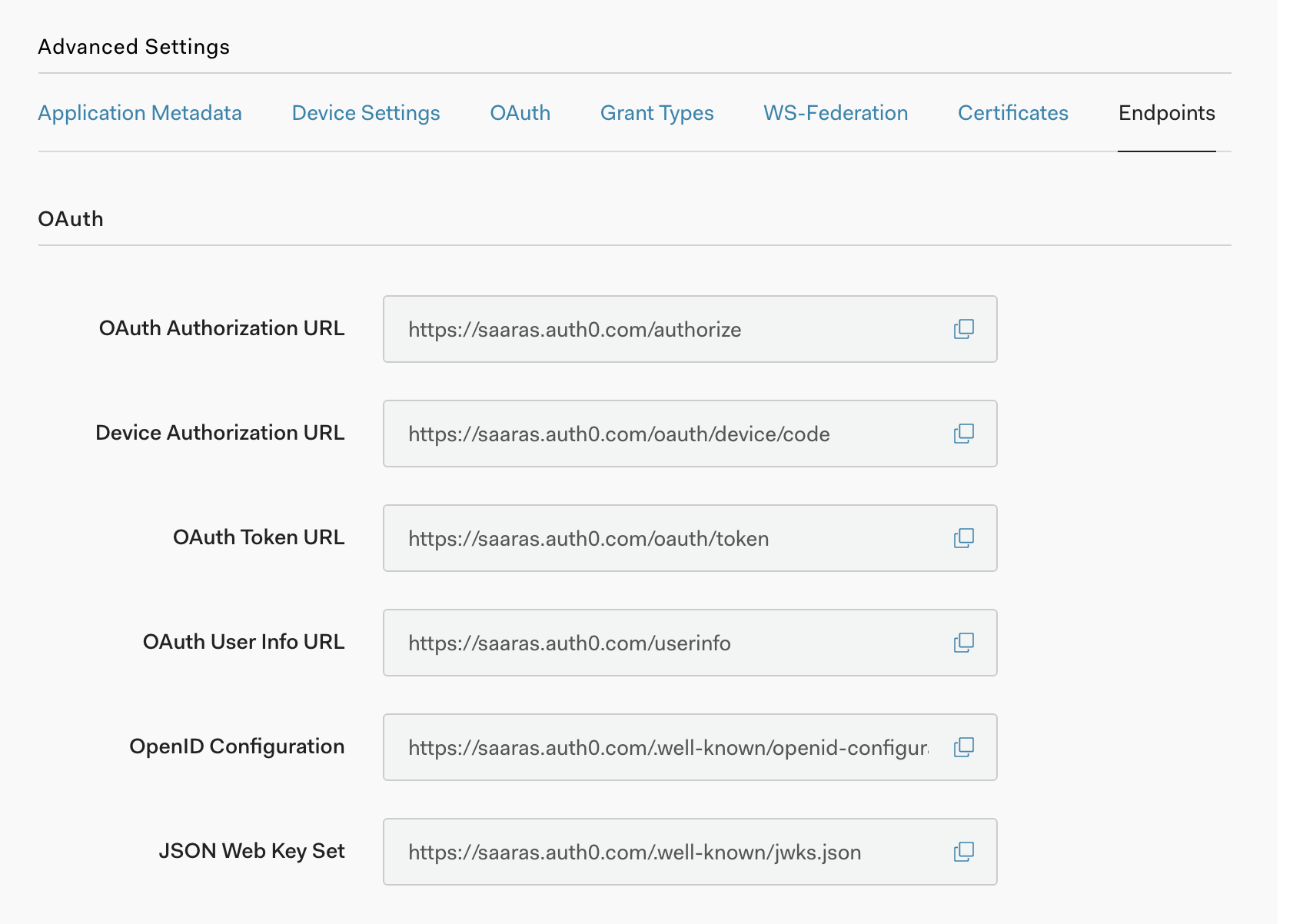
Note the JSON Web key set configuration for Auth0 above. These values are provided to filter config
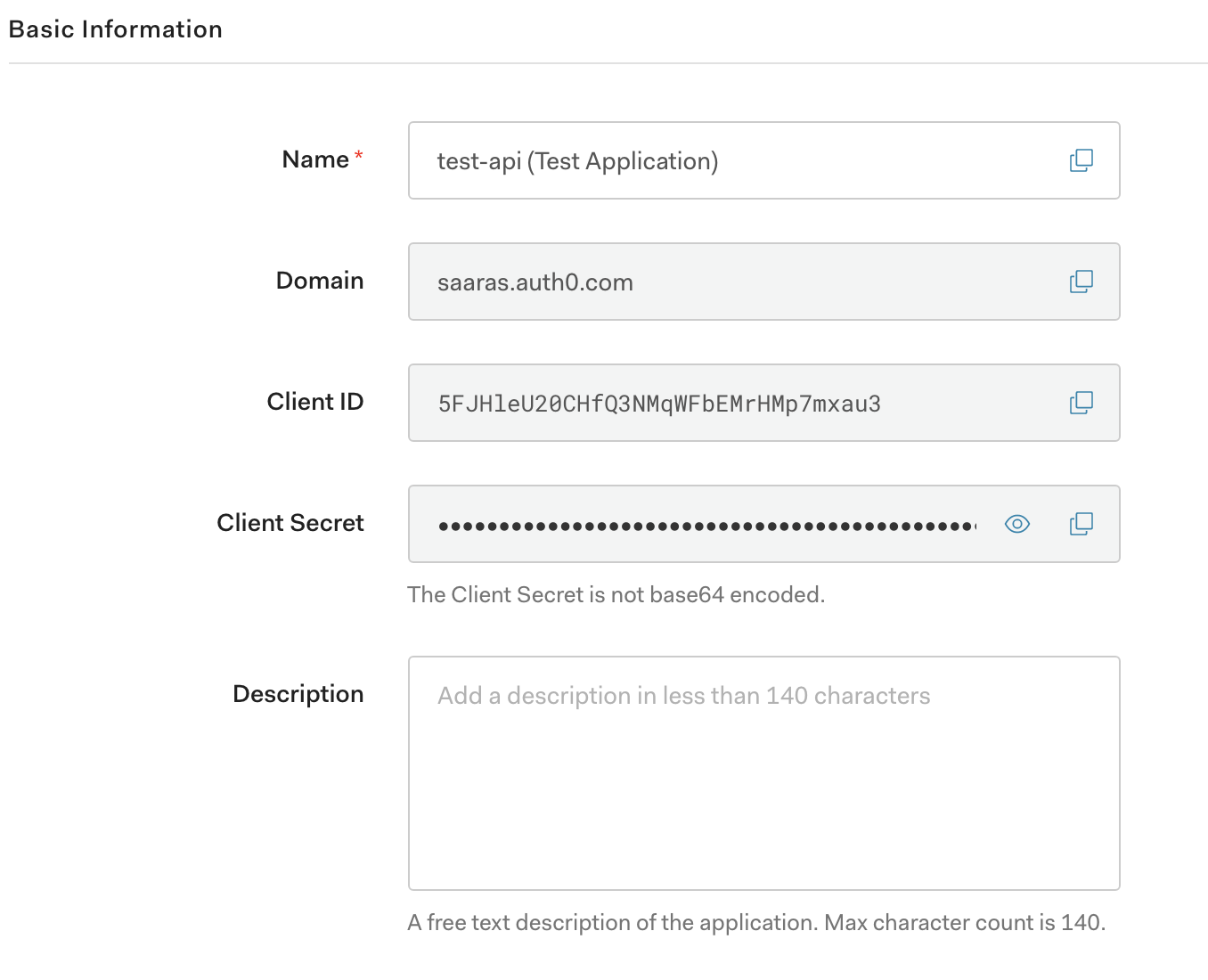
Note the Domain configuration for auth0 above. These values are provided to filter config
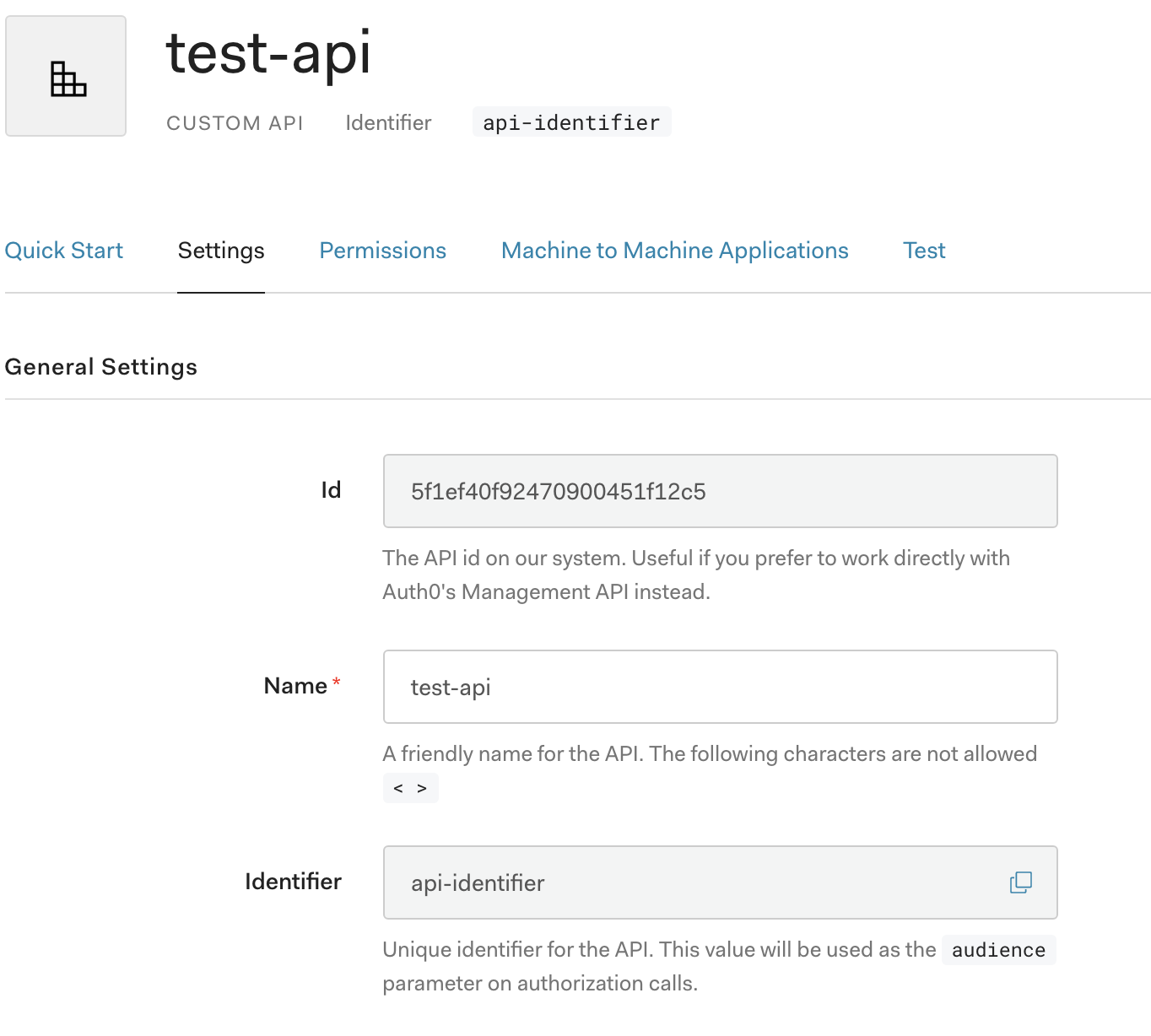
Note the Identifier configuration for auth0 above. These values are provided to filter config
---
apiVersion: enroute.saaras.io/v1
kind: HttpFilter
metadata:
labels:
app: httpbin-app
name: httpbin-80-jwtfilter
namespace: httpbin
spec:
enrouteConfigScope: ["enroute1"]
httpFilterConfig:
config: |
{
"name" : "auth0",
"jwks_uri" : "https://saaras.auth0.com/.well-known/jwks.json",
"audience" : "api-identifier",
"issuer" : "https://saaras.auth0.com/",
"route" : [{"prefix" : "/"}],
"jwt_service_name" : "externalauth",
"jwt_service_port" : 443,
"jwt_forward_header_name" : "x-jwt-token"
}
name: httpbin-80-jwtfilter
services:
name: externalauth
port: 443
protocol: tls
type: http_filter_jwt
---
Notes
JWT plugin is a global HttpFilter. It sets configuration on the Listener and is applicable to all GatewayHost when defined.