Integration with HashiCorp Vault
EnRoute Technical Reference
Integration with HashiCorp Vault
What is HashiCorp Vault ?
HashiCorp vault is responsible for protecting sensitive data like passwords, API Keys, credentials, license keys, SSH Keys, RSA Tokens, TLS Certificates.
When a connection is terminated using Enroute, it needs a TLS Certificate installed on the GatewayHost Enroute integrates with HashiCorp Vault to use TLS Certificates stored in Vault.
Apart from storing secrets, they should be reliably transmitted. Vault defines interfaces to securly store and retrieve secrets.
Interfacing Vault
Vault uses a Secret Engine to store, generate and encrypt data. Secret engines use a path to demux incoming requests. We’ll use the Key/Value secret engine interface . This needs that when Enroute interfaces Vault, it uses the appropriate path to communicate with Vault.
Standalone Gateway Integration with Vault
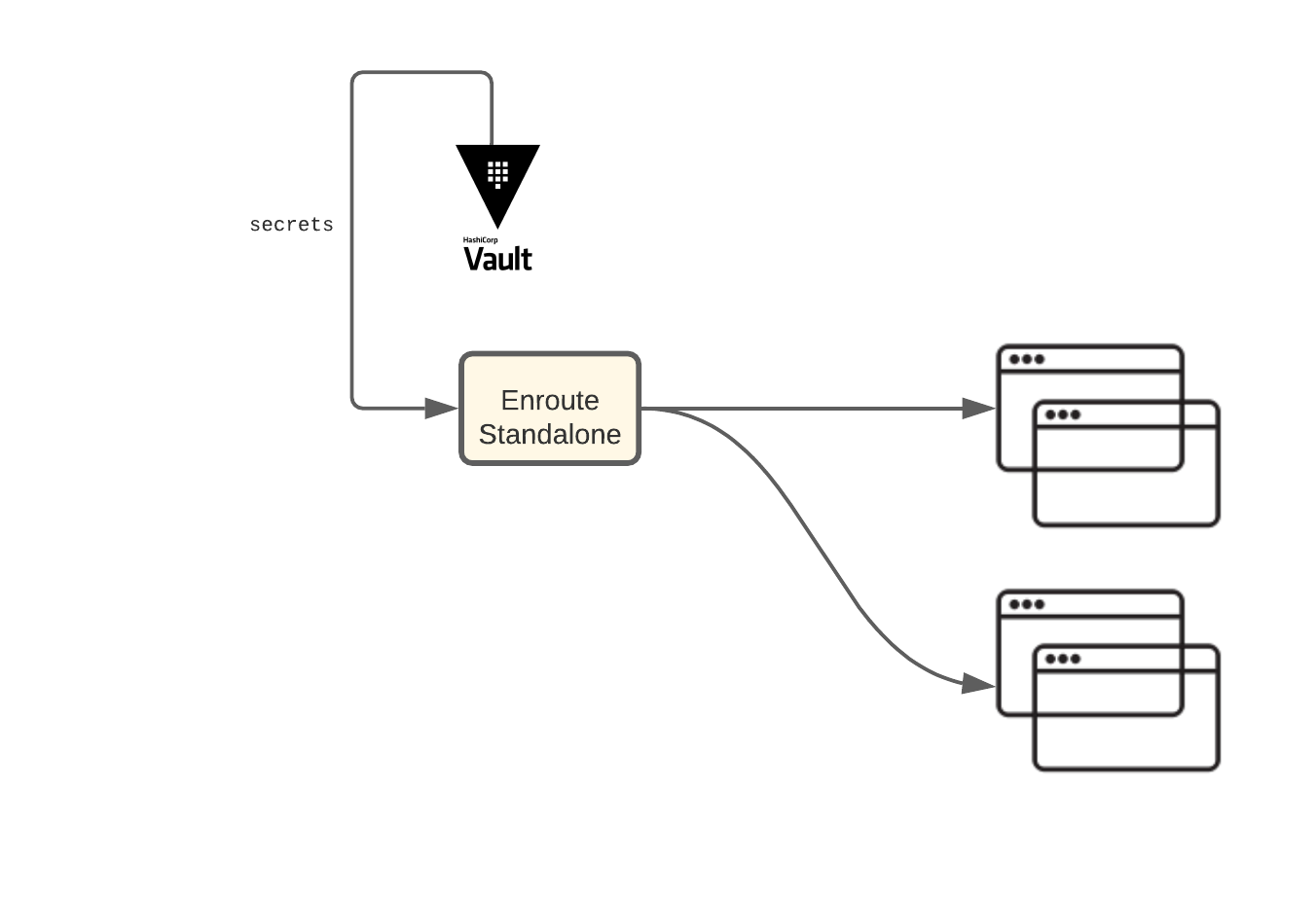
The standalone gateway when provided with vault globalconfig uses it to fetch secrets from the vault store.
Keys to use for secret creation
Secrets can be stored in Vault using a Key/Value . Enroute needs the TLS Certificate and TLS Key from vault. But prior to that they should be stored in Vault.
The key used to store these artifacts are configurable in the GlobalConfig for Vault integration with Enroute. The key used for certificates is should match what is specified in valut_certificate_key and the key used for TLS Key should match what is specified for vault_tlskey_key . The Key/Value must be stored base64-encoded in the data.
For example here is an example of how to store the Certificate and Key in Vault when vault_certificate_key is set to application-tls-cert and vault_tlskey_key is set to application-tls-key
map under the certificate and key keys respectively
curl -X POST \
-H "Content-Type: application/json" \
-H "X-Vault-Token: <Vault token>" \
-d '{"data": {"application-tls-cert": "<base64-encoded certificate>", "application-tls-key": "<base64-encoded key>"}}' \
http://127.0.0.1:8200/v1/secret/data/enroutedemo.comVault Integration Filter Configuration
Vault Integration global configuration needs the following config
Vault Filter config
| Field | Description |
|---|---|
| vault_uri | URI Location of Vault Service |
| vault_token | Access token needed to interface the Vault key/value secret engine |
| vault_kv_path | Path that will be used to access the key/value secret engine |
| vault_sync_interval | Value in seconds used by Enroute to synchronize secrets from vault |
| vault_refresh_interval | Value in seconds used by Enroute to perform a complete referesh |
| vault_certificate_key | Certificate to use to fetch the certificate from vault store |
| vault_tlskey_key | Key to use to fetch the certificate from vault store |
| vault_check_secret_expiry | Bool value to indicate if the TLS certificate read from valut should be validated for expiry. |
Vault Filter Example
GLOBALCONFIG_NAME="hashicorp_vault_secret_store"
GLOBALCONFIG_TYPE="globalconfig_vault"
GLOBAL_CONFIG='
{
"vault_uri" : "https://10.0.0.10:8200/",
"vault_token" : "s.5bVxPc90f4GlQMKrupuWq7CH",
"vault_kv_path" : "/v1/secret",
"vault_sync_interval" : 5,
"vault_refresh_interval" : 120,
"vault_certificate_key" : "application-tls-cert",
"valut_tlskey_key" : "application-tls-key",
"vault_check_secret_expiry" : true
}'
curl -s -X POST localhost:1323/globalconfig \
-d "globalconfig_name=${GLOBALCONFIG_NAME}" \
-d "globalconfig_type=${GLOBALCONFIG_TYPE}" \
-d "config"="${GLOBAL_CONFIG}"
Vault Plugin is in private beta
Vault Plugin is currently available in private beta. If you’d like to evaluate it, please get in touch with us.